This article describes a critical vulnerability in a web application called “Online Shoe Store 1.0” from code-projects. Here’s a breakdown of the key points:
What is the vulnerability?
- The vulnerability is an SQL Injection in the file
/details.php. - It allows attackers to manipulate the
idargument, likely a parameter passed to the script (e.g., via a URL query string,details.php?id=123).
Why is it critical?
SQL Injection vulnerabilities can allow attackers to execute arbitrary SQL commands on the application’s database. This could lead to:
- Data theft: Extracting sensitive user information (e.g., passwords, credit card details).
- Data manipulation: Altering or deleting database records.
- Gaining control: Using SQL injection to execute commands that may allow deeper penetration into the system.
How does it work?
- The
idparameter is improperly sanitized or validated, meaning the application directly uses the input in an SQL query.
- An attacker might exploit this by crafting malicious input, such as:
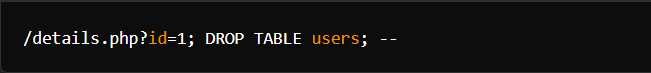
This input could trick the database into running harmful SQL commands.
Attack vector:
The attack can be initiated remotely, meaning no physical access to the server is required. This increases the threat since anyone with internet access can attempt the attack.
Public disclosure:
The exploit has been disclosed publicly, meaning detailed information about how to exploit this vulnerability is available online. This makes the system more susceptible to attacks since malicious actors can easily find and use the exploit.
Implications for the application:
- The application is at high risk of being compromised.
- If sensitive data is stored in the database, it is vulnerable to theft or destruction.
- The website or the entire system could be taken down or defaced.
What to do about it?
- Patch immediately: If the developers have released a fix or an update, apply it as soon as possible.
- Sanitize inputs: Ensure all user inputs are properly validated and sanitized to prevent malicious input.
- Use prepared statements: Avoid directly embedding user input in SQL queries. Use parameterized queries or prepared statements instead.
- Monitor for attacks: Keep logs and monitor suspicious activity to detect and respond to potential exploits.
- Educate and audit: Train developers on secure coding practices and regularly audit code for vulnerabilities.
This vulnerability represents a significant security risk, and immediate action should be taken to address it.