In the realm of web security, SQL Injection (SQLi) is one of the most dangerous vulnerabilities that can compromise the confidentiality, integrity, and availability of an application. Recently, a critical SQL injection vulnerability was discovered in SourceCodester Kortex Lite Advocate Office Management System 1.0, specifically in the edit_case.php file. This vulnerability allows an attacker to manipulate the ID argument to inject arbitrary SQL queries, potentially leading to data theft, unauthorized access, and complete database compromise.
In this article, we will discuss the nature of this vulnerability, how SQL injection works, the possible impacts, and how organizations can mitigate such threats effectively.

What is SQL Injection?
SQL Injection (SQLi) is a web security vulnerability that allows an attacker to interfere with an application’s database queries. When an application does not properly sanitize user inputs before passing them into an SQL query, an attacker can inject malicious SQL statements to manipulate the database.
SQLi can be used to:
- Access unauthorized data (e.g., retrieving other users’ case details).
- Modify or delete records (e.g., changing case statuses or deleting legal documents).
- Execute administrative operations on the database (e.g., creating new admin users or dumping the entire database).
- Bypass authentication by modifying login credentials stored in the database.
Breakdown of the Vulnerability in Kortex Lite Advocate Office Management System
Affected Component
The vulnerability exists in the file edit_case.php, which is responsible for modifying case details within the Advocate Office Management System.
Vulnerable Parameter
The attack exploits the ID parameter. This parameter is supposed to take a legitimate case ID from the user to fetch case details. However, due to improper input validation, an attacker can inject malicious SQL queries into this parameter.
How the Attack Works
Consider the following vulnerable SQL query inside edit_case.php:
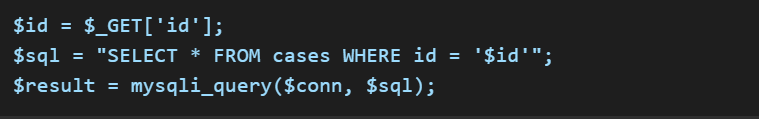
Here, the application retrieves the ID from the user’s request ($_GET['id']) and directly inserts it into an SQL query. If the user inputs malicious SQL code, the query gets altered.
For example, an attacker could pass the following input:

This would turn the query into:
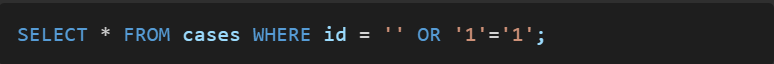
Since '1'='1' is always true, the query returns all records from the cases table, exposing all case details.
Remote Exploitation
- Since this vulnerability exists in a publicly accessible script (
edit_case.php), an attacker does not need any prior authentication. - It can be exploited remotely via a web browser or automated tools like SQLmap.
- The exploit has already been publicly disclosed, making it easier for malicious actors to use it.
Real-World Implications of This Vulnerability
Data Breach
- Attackers can extract confidential legal data, including case files, client records, and attorney details.
- Sensitive client information could be leaked or sold on dark web marketplaces.
Unauthorized Modifications
- Attackers can modify legal cases, changing their status or manipulating case outcomes.
- Evidence could be tampered with, leading to incorrect legal decisions.
Privilege Escalation
- By exploiting SQLi, an attacker could modify user roles and grant themselves administrator privileges.
- This could lead to complete compromise of the system.
Complete System Takeover
- If the attacker gains access to system credentials stored in the database, they can take full control of the web application.
- They can even plant backdoors to maintain persistent access.
Demonstration: Proof-of-Concept (PoC) Exploit
Testing the Vulnerability with SQLmap
An attacker or a security researcher can use SQLmap, an automated SQL injection tool, to exploit this vulnerability.
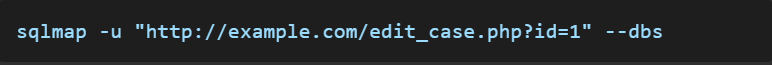
This command will check if the ID parameter is vulnerable and list the databases.
Manually Injecting Malicious SQL
A direct test can be performed using a web browser:
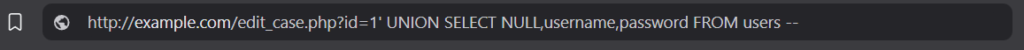
This would return usernames and hashed passwords from the users table, allowing the attacker to crack passwords offline.
Mitigation Strategies
Use Parameterized Queries
The best way to prevent SQL injection is to use prepared statements.
Vulnerable Code:
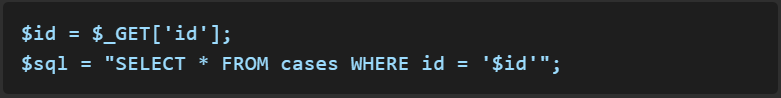
Secure Code:
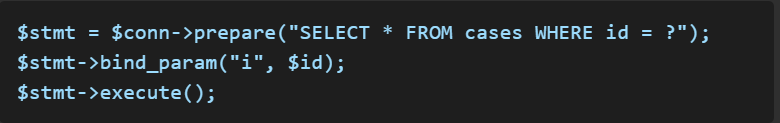
Input Validation and Sanitization
- Restrict input fields to allow only numeric values for ID parameters.
- Use
htmlspecialchars()to escape special characters.
Implement a Web Application Firewall (WAF)
A WAF can detect and block SQL injection attempts in real-time.
Least Privilege Principle
- Limit the database user’s permissions to prevent modification of critical tables.
- Separate read and write privileges for different database operations.
Update and Patch
- Apply security patches provided by SourceCodester.
- Keep PHP and MySQL updated to prevent zero-day vulnerabilities.
Conclusion
The SQL injection vulnerability in SourceCodester Kortex Lite Advocate Office Management System 1.0 is a critical security risk that can be remotely exploited. Since an exploit has been publicly disclosed, systems running this vulnerable software are at high risk.
To mitigate this risk, developers must implement parameterized queries, enforce input validation, deploy web application firewalls (WAFs), and follow best security practices.
SQL injection remains one of the most common attack vectors in web applications, but by following secure coding practices, we can eliminate these risks and protect sensitive legal data from falling into the wrong hands.